https://habr.com/en/company/roi4cio/blog/526302/- ROI4CIO corporate blog
- Information Security
- Software
Modern corporate IT infrastructure consists of many systems and components. And monitoring their work individually can be quite difficult — the larger the enterprise is, the more burdensome these tasks are. But there are the tools, which collect reports on the work of the entire corporate infrastructure — SIEM (Security Information and Event Management) system in one place. Read the best of such products according to Gartner experts in our review, and learn about the main features from our comparison table.
In a few words, SIEM technology gives administrators an overview of what's happening on the network. Such systems in real time provide an analysis of security events, as well as the activity of devices and users, which helps to respond to them before significant damage is done. SIEM programs collect information from servers, domain controllers, firewalls and many other network devices and provide it in the form of convenient reports. This data is not necessarily associated with security. With their help, for example, it is possible to understand how the network infrastructure functions and how to develop a plan for its optimization. But the main thing, of course, is the detection of potential gaps, as well as the localization and elimination of existing threats. Such data is provided through the collection and combination of network device log data. The identification and classification of events occurs after collecting information (this procedure occurs automatically at specified intervals). Then (again, in accordance with the specified settings) the notifications are sent that certain actions of the equipment, programs or users may be potential security problems.
What opportunities are opening up? SIEM helps to solve a number of problems. Among them: timely detection of targeted attacks and unintentional violations of information security by users, assessing the security of critical systems and resources, conducting incident investigations, and much more. At the same time, SIEM platforms have a number of limitations. For example, they do not know how to classify data, they often work poorly with e-mail, they have blind spots in relation to their own events. And, of course, they cannot fully cover the information security issues at the enterprise. But along with this, they are an important part of the enterprise security system, although not a critical one. Moreover, the development of SIEM platforms does not stand still. For example, some modern products have analytical functions, that is, they not only issue the reports and indicate the potential problems, but also know how to analyze events themselves and make decisions on informing about certain events. In any case, when choosing a specific product, you should focus on many parameters, among which we highlight the centralized collection, processing and storage of information, notification of incidents and data analysis (correlation), as well as the coverage of the corporate network. And, of course, if possible, before buying, it is worth launching a trial/demo version and see how it is suitable for the company.
IBM QRadar Security Intelligence
The SIEM platform from IBM is one of the most advanced on the market: even in the Gartner leader’s quadrant it is ahead of the competitors and has been successively there for 10 years. The product consists of several systems integrated among themselves, which together provide the maximum coverage of events occurring in the network, and many functions work directly out of the box. The tool can collect data from a variety of sources, for example, operating systems, security devices, databases, applications and many others.
QRadar Security Intelligence can sort events by priority and highlight those that pose the greatest security risk. This is due to the functions of analyzing the anomalous behavior of objects (users, equipment, services and processes in the corporate network). In particular, the actions related to accessing the suspicious IP addresses or requests from them are determined. The detailed reports are provided for all suspicious actions, which, for example, makes it possible to detect suspicious actions out of hours. The similar approach in combination with users monitoring functions and a visual representation of the network at the application level allows you to deal with insider threats. In addition, with ordinary cyberattacks, information comes in very quickly and helps to prevent them before they reach their goals and cause significant damage.
Risk-based discovery and prioritization using advanced analysis and correlation between assets, users, network activity, vulnerabilities, threat analysis, etc. are the main features of IBM QRadar Security Intelligence. IBM QRadar can chain events together, creating a separate process for each incident. Due to the fact that information is collected and displayed on the screen in one place, the administrator can see all the associated suspicious actions, detected by the system. And new related events are added to a single chain, so analysts should not switch between multiple alerts. And for deeper investigations, the special tool IBM QRadar Incident Forensics can restore all network packets, associated with the incident, and recreate the attacker's actions step-by-step.

Splunk Enterprise Security
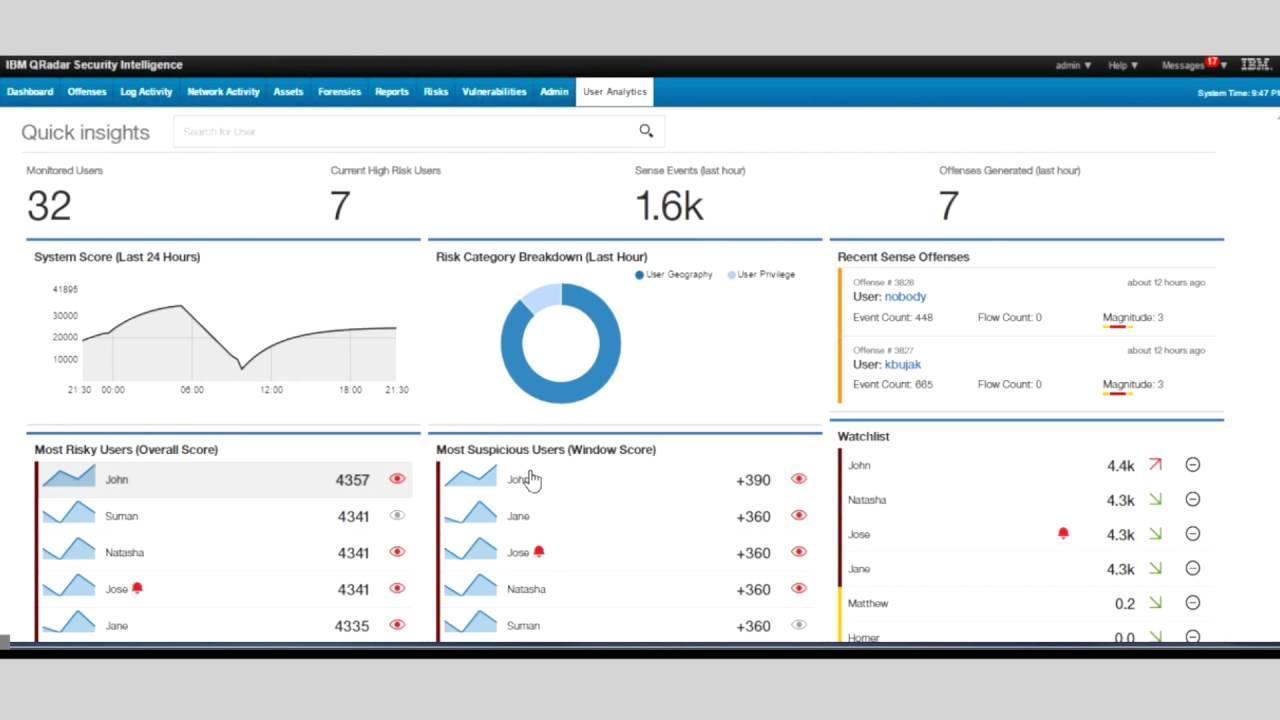
This is one of the industry leading platforms, a distinctive feature of which is a wide list of sources of information with which it works. Splunk Enterprise Security can collect event logs from traditional network components (servers, security devices, gateways, databases, etc.), mobile devices (smartphones, laptops, tablets), web services and distributed sources. Information collected: data on users actions, logs, diagnostic results, etc. This allows for convenient search and analysis in automatic and manual mode. The solution has many customizable notifications, which, based on the information collected, warn of existing threats and report the potential problems in advance.
The product consists of several modules, which are responsible for conducting investigations, logical circuits of protected resources and integration with many external services. This approach makes it possible to conduct a detailed analysis of the variety of parameters and establish a relationship between events, which, at first glance, do not correlate with each other. Splunk Enterprise Security helps to compare data by time, location, created requests, connection to a variety of systems and other parameters.
The tool also knows how to work with large data arrays and is a full-fledged Big Data platform. Large arrays of data can be processed both in real time and in historical search mode, and, as mentioned above, a huge number of data sources are supported. The Splunk Enterprise Security can index hundreds of TB of data per day, so it can be used on enterprise networks of very large sizes. The special MapReduce tool allows you to quickly scale the system horizontally and evenly distribute the load, so that system performance always remains at the acceptable level. At the same time, configurations for clustering and disaster recovery are available to users.

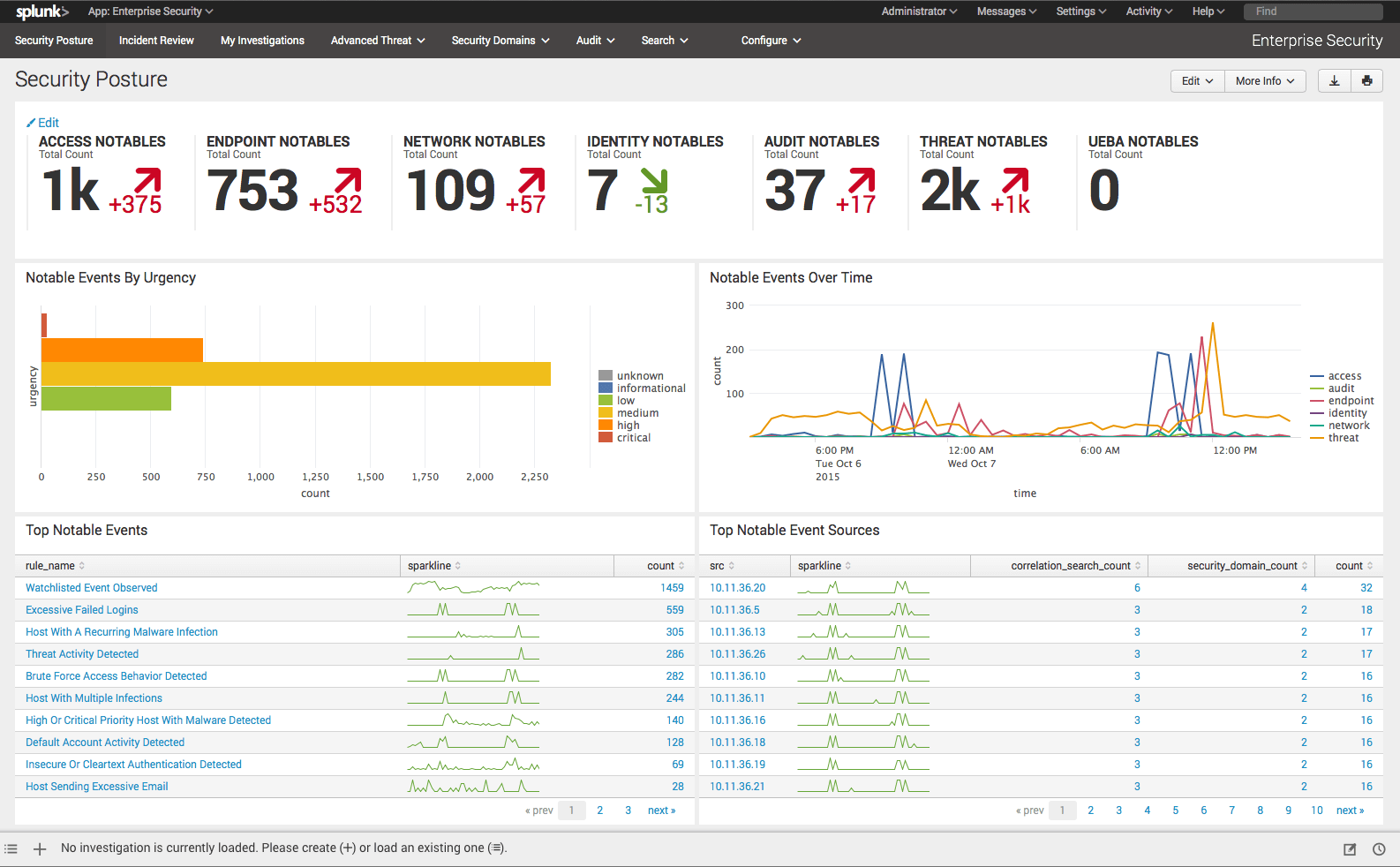
McAfee Enterprise Security Manager
The McAfee solution comes in both physical and virtual devices, as well as software. It consists of several modules, which can be used both together and separately. The Enterprise Security Manager provides the continuous monitoring of corporate IT infrastructure, collects information about threats and risks, helps to prioritize threats and quickly conduct investigations. For all incoming information, the solution calculates the basic level of activity and pre-creates notifications, which will be received by the administrator, if the scope of this activity is violated. Also, the tool can work with context, which significantly expands the analysis and detection of threats, as well as reduces the number of false signals.
The McAfee ESM integrates well with third-party products without an API, making the product compatible with many other popular security solutions. It also has support for the McAfee Global Threat Intelligence platform, which extends the traditional SIEM functionality. Thanks to it, ESM receives the constantly updated threat information from around the world. In practice, this makes it possible, for example, to detect events, which are associated with suspicious IP addresses.
The developer offers his clients a set of McAfee Connect tools to improve the system performance. These tools contain the ready-made configurations, which help to perform the complex scenarios for using the SIEM system. For example, a package of materials on analyzing the users behavior helps to find hidden threats better and faster, makes security operations more accurate and significantly reduces the time of investigation of incidents. The package for Windows helps to monitor the services of this OS to assess their proper use and detection of threats. In total, more than 50 packages are available for different scenarios, products and standards.

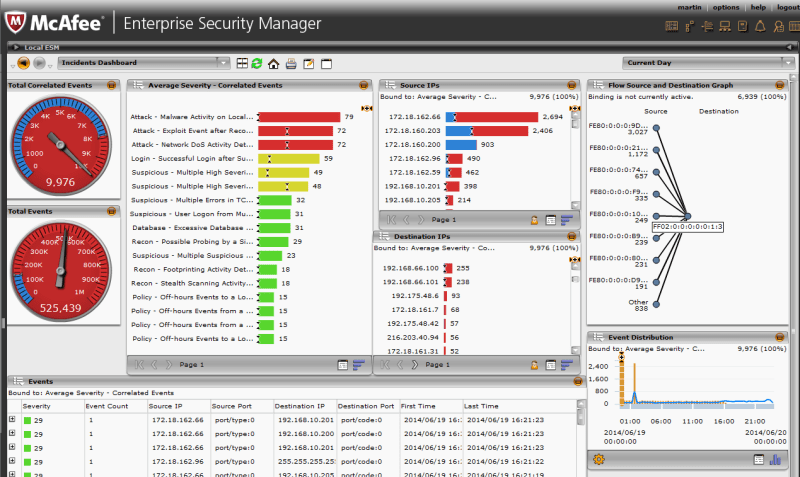
AlienVault Unified Security Platform
AlienVault Company has recently teamed up with AT&T Business under the AT&T Security brand, but its main product is still sold under the old name. This tool, like most other platforms from the review, has broader functionality than the traditional SIEM. Specifically, AlienVault USM has various modules, responsible for asset control, full packet capture, etc. The platform also knows how to test the network for vulnerabilities, and this can be either a one-time check or continuous monitoring. In the latter case, the notifications of the new vulnerability arrive almost simultaneously with their appearance.
Among other features of the platform: an infrastructure vulnerability assessment, which shows how secure the network is and if its configuration meets security standards. The platform is also able to detect attacks on the network and timely notify about them. In this case, the administrators receive detailed information about where the invasion is coming from, what parts of the network have been attacked and what methods the attackers are using, as well as what needs to be done first for reflection. In addition, the system is able to detect the insider attacks from within the network and notify about them.
With the proprietary AlienApps solution, the USM platform integrates with many third-party security solutions and effectively complements them. These tools also expand the capabilities of AlienVault USM in the field of security settings and automated response to threats. Therefore, almost all information about the security status of the corporate network becomes available directly through the platform interface. These tools also make it possible to automate and organize response when threats are detected, which greatly simplifies and accelerates their detection, as well as incident response. For example, if a connection with a phishing site is detected, the administrator can send data to the third-party DNS protection service to automatically block this address — this way, it will become inaccessible for visiting from computers within the organization.

Micro Focus ArcSight Enterprise Security Manager
Micro Focus's SIEM platform, which HPE developed until 2017, is a comprehensive tool for detecting, analyzing and managing workflows in real time. The tool provides massive opportunities to collect information about the status of the network and the processes occurring in it, as well as a large set of ready-made sets of security rules. Many features in ArcSight Enterprise Security Manager work automatically, including, for example, the identifying threats and prioritizing. For investigations, this tool can integrate with another proprietary solution — ArcSight Investigate. With it, you can detect unknown threats and perform a quick intelligent search, as well as visualize data.
The platform can process information from the most diverse types of devices according to the developers, there are more than 500 of them. Its mechanisms support all common event formats. The information collected from network sources is converted into a universal format for use on the platform. This approach helps quickly to identify situations, which require investigation or immediate action and helps administrators to focus on the most pressing high-risk threats.
For companies with extensive networks of offices and divisions, ArcSight ESM proposes to use the SecOps work model when remote security groups are combined and can exchange reporting, processes, tools and information in real time. Therefore, for all departments and offices, they can apply the centralized sets of settings, policies and rules, use the unified matrix of roles and access rights. This approach helps to quickly respond to threats in any part of the company.


RSA NetWitness Platform
The platform from RSA Company (one of Dell divisions) is a set of modules, which provide the threat visibility based on data from various network sources: endpoints, NetFlow, security devices, information from transmitted packets, etc. For this, a combination of several physical and/or virtual devices, which process information in real time and issue warnings based on it, and also store data for future investigations. Moreover, the developer offers architecture for both small companies and large distributed networks.
The NetWitness Platform can detect insider threats and works with contextual information about the specific infrastructure, which provides prioritizing alerts and optimizing work in accordance with the specifics of the organization. The platform is also able to correlate information about individual incidents, which helps to determine the full extent of attacks on the network and configure it in such a way as to minimize such risks in the future.
The developers pay much attention to working with endpoints. Thus, RSA NetWitness Platform has a separate module for this, which ensures their visibility both at the user's level and at the kernel-level. The tool can detect the abnormal activity, block the suspicious processes and assess the degree of vulnerability of a particular device. And the collected data is taken into account in the operation of the entire system and also affect the overall assessment of network security.

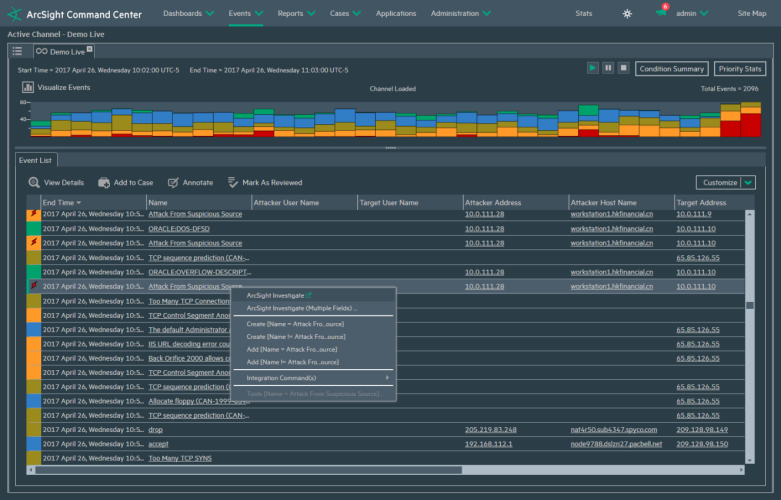
FireEye Helix Security Platform
The FireEye’s cloud platform allows organizations to monitor any incidents, from alerting to remedying the situation. It combines many branded tools and can integrate with third-party products. The Helix Security Platform makes extensive use of users behavior analytics, which recognizes the insider threats and attacks, not related to malware.
In order to counter threats, the tool not only uses the alerts from administrators, but also applies the predefined rule sets, of which there are about 400. This minimizes the number of false positives and frees administrators from constant checks of threat messages. In addition, the system offers the ability to conduct investigations and search for threats, behavioral analysis, support for multiple resources for obtaining information, and convenient management of the entire security complex.
The tool does a good job of detecting advanced threats. The Helix Security Platform arsenal has the ability to integrate more than 300 security tools from both FireEye and third-party manufacturers. By analyzing the context of other events, these tools provide a high level of detection of hidden and disguised attacks.

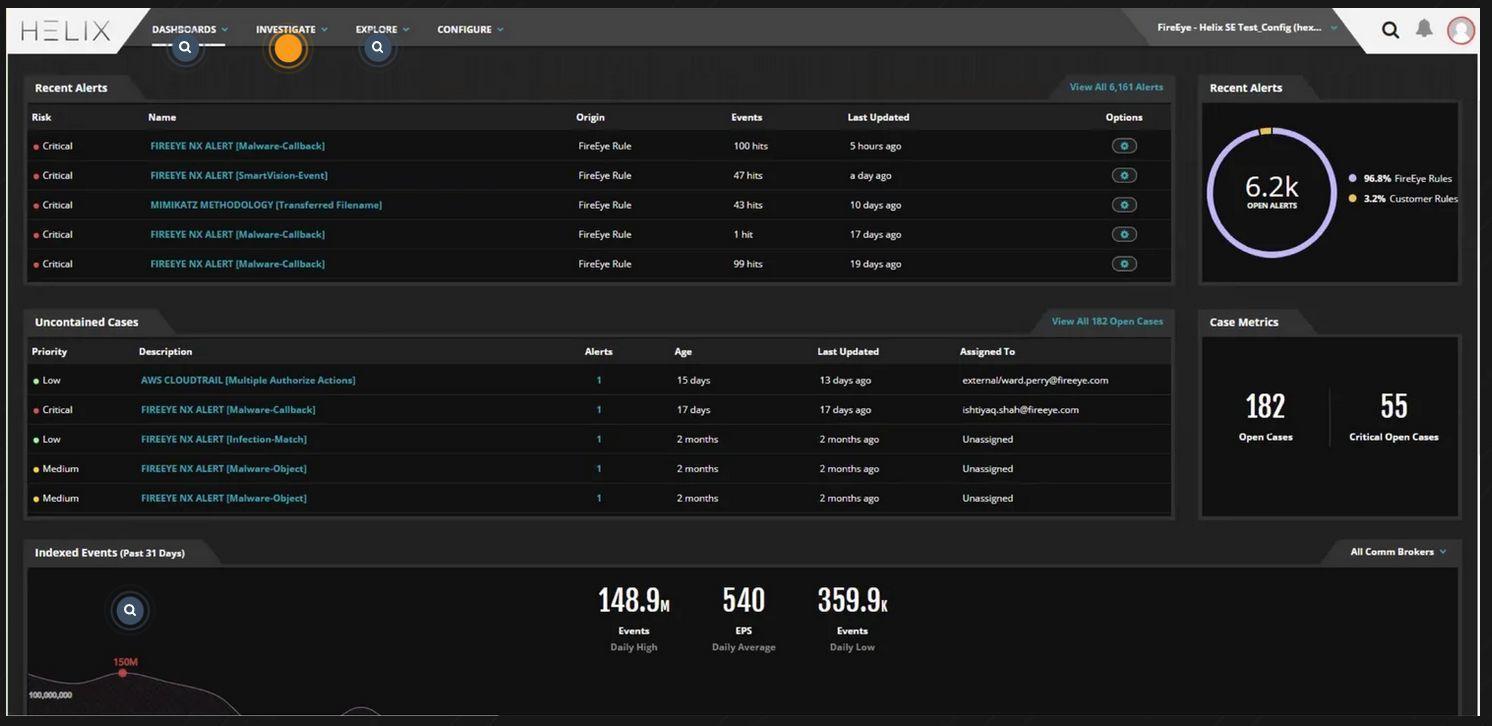
Rapid7 insightIDR
Rapid7 Company offers its clients a cloud-based SIEM platform, created for behavior analysis. The system conducts the in-depth analysis of logs and journals, and also sets up special traps to detect illegal intrusions into the network. The InsightIDR tools constantly monitor the users activities and correlate them with online events. This not only helps to identify insiders, but also prevents the intentional security breaches.
The Rapid7 insightIDR constantly monitors endpoints. This makes it possible to see the unusual processes, atypical users behavior, strange tasks, etc. If such actions are detected, the system helps to check whether they are repeated on other computers or remain a local problem. And in case of problems and investigation of incidents, a visual tool is used. It conveniently organizes the accumulated data over time and greatly simplifies the investigation.
To better counter threats, the developer's experts can independently assess the degree of security of the corporate environment, from equipment to current processes and policies. Thanks to this, it is possible to build an optimal network protection scheme from scratch using Rapid7 insightIDR or to improve the existing work schemes.

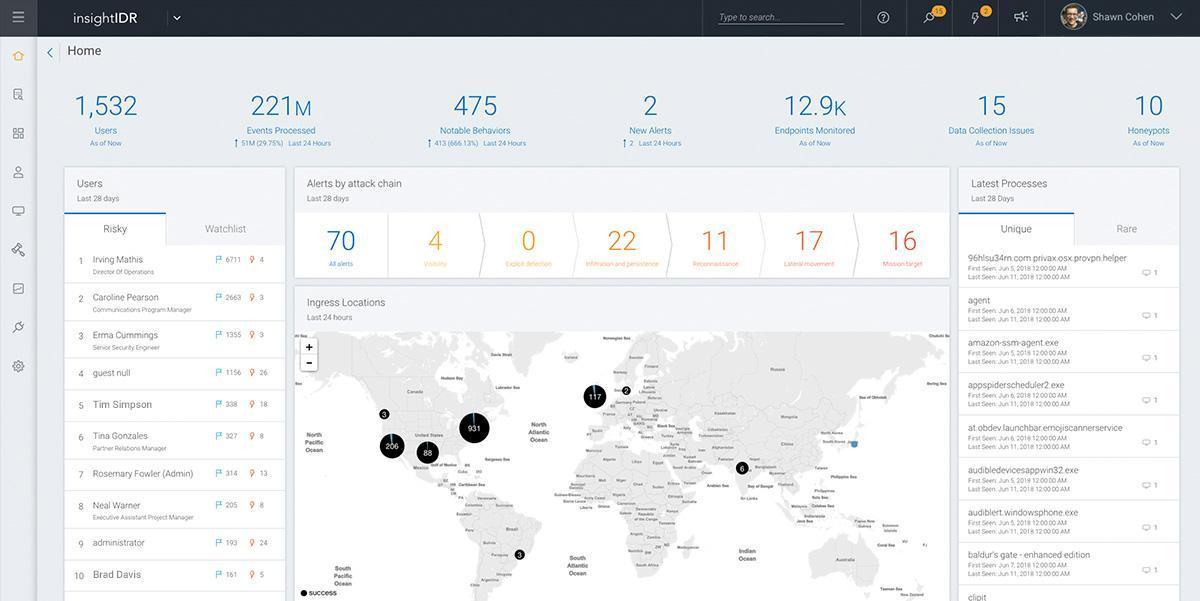
Fortinet FortiSIEM
Fortinet's comprehensive and scalable solution is a part of the Fortinet Security Fabric platform. The solution comes in the form of physical devices, but can also be used on the basis of a cloud infrastructure or as a virtual device. The tool provides a wide coverage of information sources — more than 400 devices from other manufacturers are supported. These include the endpoints, IoT devices, applications, security features, and more.
The platform is able to collect and process information from endpoints, including file integrity, registry changes, installed programs and other suspicious events. The FortiSIEM has in-depth analysis tools, including real-time event search as well as past events, attribute and keyword searches, dynamically changing tracking lists, which are used to detect critical violations and much more.
The tool provides administrators with full-featured, customizable dashboards, which greatly enhance the system usability. They have the ability to play slide shows to demonstrate the performance of systems, there is the possibility of generating a variety of reports and analytics, and color marking is used to highlight critical events.

Instead of an afterword
The market has a very large number of SIEM solutions, most of which are very functional. Often their capabilities go beyond the standard definition of SIEM and offer сlients a wide variety of network management tools. Moreover, many of them work directly out of the box, requiring minimal intervention during installation and initial configuration. But there is an obstacle: they can vary in dozens of small parameters, talking about which within a single review is not possible. Therefore, in each case, it is necessary to choose a solution not only relying on the basic needs of the enterprise, but also to take into account the small details and the future growth of the organization. We have drawn your attention to the main points, and testing of trial versions of products will help to carefully understand the details and nuances. Fortunately, almost all vendors provide this opportunity.


















